Intellectual property theft (Case 1)
Intellectual property theft happened in a service based company situated in New Delhi. The complainant complains that some of the company’s employee had used the company’s infrastructure and stolen the clients data which include Name, Phone numbers, email address, Date of Births with home address.
Investigation Process
After receiving the complaint a agent based application deployed in corporate network on each system using active directory. Searched few relevant keywords and Hash values of sample files. Out of 100s systems two detected positive. Forensic imaging done using the deployed application. When email database was analyzed found that some emails were forwarded on personal email addresses which were not permitted in office. Also Pen drive logs detected. Also found that few files time stamps changed at the same time when pen drives was plugged. On the basis of Pen drive serial number company security team recovered one pen drive in suspect’s beg. Forensic analysis done of pen drive and recovered the same data which was available in companies computer system.
Altered Evidence and Spoliation (Case 2)
Electronic evidence in the form of word processing documents which were submitted by a party in litigation are alleged to be altered. Altered electronic evidence has become a common claim with the ability to determine the changes becoming more difficult. How do you know if an e-mail has been altered? What about a text document?
Investigation Process
All evidence needs to be validated for authenticity. The weight given in legal hearings depends upon the veracity of the evidence. Many electronic files can be quickly validated through hash comparisons (HashMyFiles). An example below shows two files with different file names, yet their hash values are identical. If one file is known to be valid, perhaps an original evidence file, any file matching the hash values would also be a valid and unaltered copy of the original file.
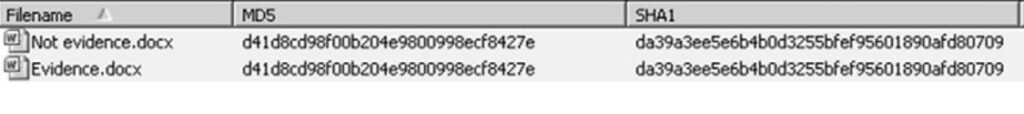
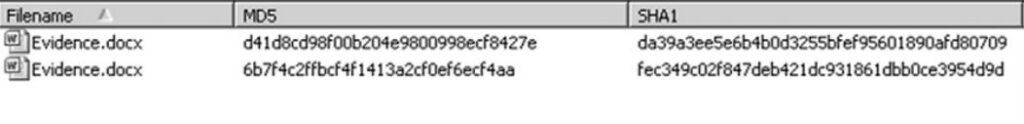
Alternatively, the below figure shows two files with the same file name but having different hash values. If there were a claim that both of these files are the same original files, it would be apparent that one of the files has been modified.
Disgruntled Employee Steals and Deletes Employer’s Data (Case 3)
Collecting information about any attached USB storage devices across a broad spectrum of computers allows you to build a timeline of device travel across the computers. As an example, a suspect using his own flash drive to copy files by connecting the flash drive to a coworker’s computer leaves traces of that activity on the coworker’s computer. One of the artifact traces is the serial number of the flash drive. It would be expected that the suspect would have connected that same USB device in his own assigned workstation or his personally owned computer before copying the files and certainly after copying the files.
Investigation Process
Below figure shows a collection of information about USB devices obtained from a computer system. If a different computer system showed any of the same devices, then those devices were connected to both systems. As the time stamps of connection are available, an analysis of the files created or accessed after the device being connected can show the files that may have been copied.
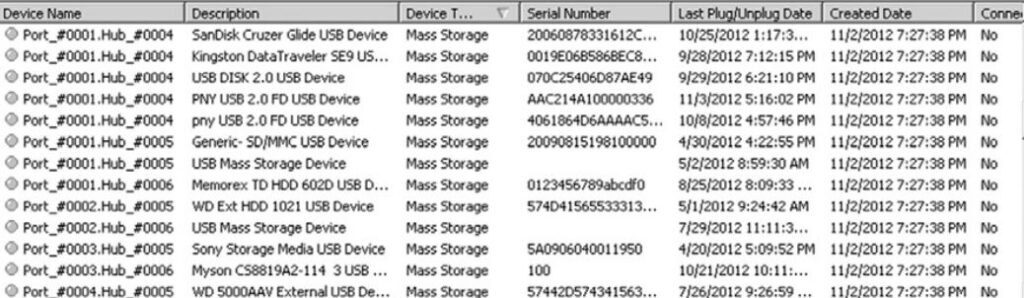
Detailed forensic analysis can be performed using any digital forensic tool to see the time stamps of copied files. Time stamps matching with USB device connections, shows that those lists of files were copied.

